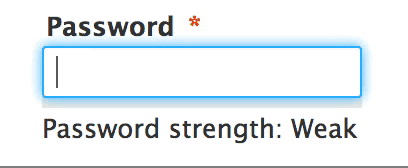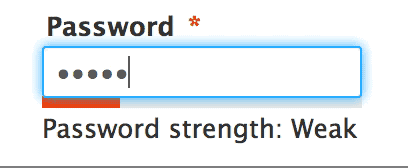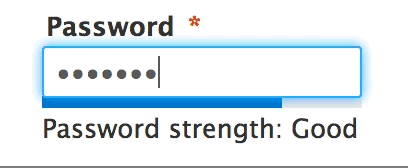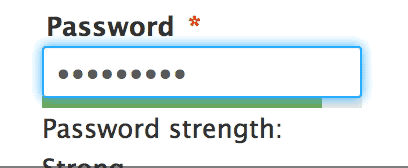
It is very important to not reuse passwords across sites, as a data breach on one site can cause a ripple effect as hackers try your logins they have gathered from one site on other sites.
And breaches happen so often that it can be hard to keep up. Recent data from Risk Based Security revealed that the number of records exposed has increased to a staggering 36 billion in 2020. There were 2,935 publicly reported breaches in the first three quarters of 2020, with the three months of Q3 adding an additional 8.3 billion records.
Here is a brief breakdown of the 10 largest breaches of the last year:
10. Microsoft – 250 million records: A simple misconfigured database security setting enabled access to a database containing email addresses, IP Addresses, and support case details. Thankfully this one did not contain passwords or credit card numbers.
9. Wattpad – 268 million records: Wattpad is a site containing user generated stories.The incident exposed extensive personal information including names and usernames, email and IP addresses, genders, general geographic location, birth dates and passwords stored in an encrypted format. This would make it difficult to obtain the password, but it is not impossible.
8. Broadvoice – 350 million records: A security researcher discovered an exposed cluster of databases from telecommunications vendor Broadvoice. One database was found to include caller names, phone numbers, and locations, among other data. Another database included transcriptions of hundreds of thousands of voicemails, many involving sensitive information such as details about medical prescriptions and financial loans.
7. Estée Lauder – 440 million records: The cosmetics giant reports that this did not contain any consumer data. The records did contain user emails in plain text, references to reports and other internal documents, IP Addresses and other confidential information. Thankfully, this one did not affect the general public.
6. Sina Weibo – 538 million records: Chinese social network Weibo was also breached. While this database did not contain credit card information, or passwords, it did contain real names, site usernames, gender, location as well as phone numbers for 172 million users.
5. Whisper – 900 million records: Whisper is a “secret-sharing” app. Their exposed data included user’s stated age, ethnicity, gender, hometown, nickname and any membership in groups, many of which are devoted to sexual confessions and discussion of sexual orientation and desires.
4. BlueKai – billions of records: Bluekai is an ad tracking service that contains profiles of users spanning multiple websites. The database held billions of records containing names, home addresses, email addresses, and web browsing activity like purchases and newsletter unsubscribes.
3. Keepnet Labs – 5 billion records: This database was managed by a U.K.-based security company, and was actually a data-breach database.
2. Advanced Info Service (AIS) – 8.3 billion records: This database appeared to be controlled by a subsidiary of this Thailand based cell phone provider. Thankfully, this database did not contain any personal information, and only contained internet usage data.
1. CAM4 – 10.88 billion records: This is an adult live-streaming website. The data contained very extensive user data. Payment logs, user names, chat logs, First and last names, Email addresses, and encrypted passwords.
One resource that I have found is the site Have I Been Pwned. This does not list all breaches, and may not have data on some that are very new, but it is an easy way to confirm if your data may be out there already.
This story originally appeared on Security Magazine.
Frankenstein Computers has been taking care of our happy clients since 1999. We specialize in IT Support, IT Service, MAC repair, PC Repair, Virus Removal, and much more. Give us a call for remote support or drop in to drop off.